As my previous topic mentioned in Blockchain POS Chains: How Infrastructure Impacts Performance, there are four pillars for the blockchain: ledger, consensus, cryptography, and smart contract. Cryptography as the fundamental technology provides truth among blockchain participants for the biggest collaboration and enables the stable operation of decentralized systems like Bitcoin, Ethereum, and others.
Let’s take a closer look at the role that cryptography plays in blockchain, and why the new 3rd gen Intel® Xeon® Scalable Processors (Ice Lake) offer the best performance for blockchain PoS.
How Cryptography Enables Blockchain
In blockchain, cryptography is used for signing, verification, encryption, hashing for functions such as keys, addresses, signatures, and transactions. For PoW blockchains such as Bitcoin and Ethereum, the blockchain community is racing to make the best performance of hashing calculation. For PoS blockchains such as Solana and Ethereum 2.0, hashing becomes not the only dominant factor. Rather, the balanced cryptography capabilities including encryption, signature, and verification will benefit the best performance for validators and RPC nodes, especially with the transaction throughput far beyond the PoW Blockchains, with TPS at 50K and above.
What Are the Common Cryptography Algorithms and Hash Functions Used in a Blockchain Transaction?
Hashing functions such as SHA256 and SHA3 are widely adopted by Ethereum and similar blockchains. SHA512 has also been introduced in some of the latest blockchains to further improve security and provide possible quantum-proof. Elliptic Curve Cryptography (ECC) is used in most blockchains for private key and public key system, with secp256k1 and Curve25519 representing the most commonly used curves offering 256 bits key size. (1)
Correspondingly, ECDSA (Elliptic Curve Digital Signature Algorithm) is the secp256k1-based signature scheme used in Blockchains such as Bitcoin and Ethereum, and EdDSA is the Curve25519-based signature scheme used in Solana and Algorand. Due to possible high TPS in Ethereum 2.0 with every node in the network potentially needing to verify millions of signatures for every epoch, it might become impossible to build a blockchain at scale. Thus the BLS (Boneh-Lynn-Shacham) signature scheme is proposed in Ethereum 2.0 in addition to ECC system.
Also, to accommodate rising performance demands for higher TPS rates, algorithms such as RSA, ECDSA, EsDSA, and AES take advantage of the AVX512 registers to keep the CPU optimized and increase memory bandwidth utilization. They provide substantial (2-10x) improvements over existing crypto algorithms.
Key Takeaway: Better Cryptography Performance in SHA512 and AVX512 Hash Functions Using 3rd Gen Intel® Xeon® Scalable Processors (Ice Lake)
As cryptography performance is critical for supporting scalable PoS blockchains, we compared the performance from newly released 3rd Gen Xeon (Ice Lake) CPUs with commercially available SHA512 and AVX512 functions as an example.
Our research indicates that the SHA512 and SHA256 crypto functions produced double the performance on other CPUs. We found similar results for ECDSA and RSA using VPMADD52 with 8x faster public key encryption and decryption.
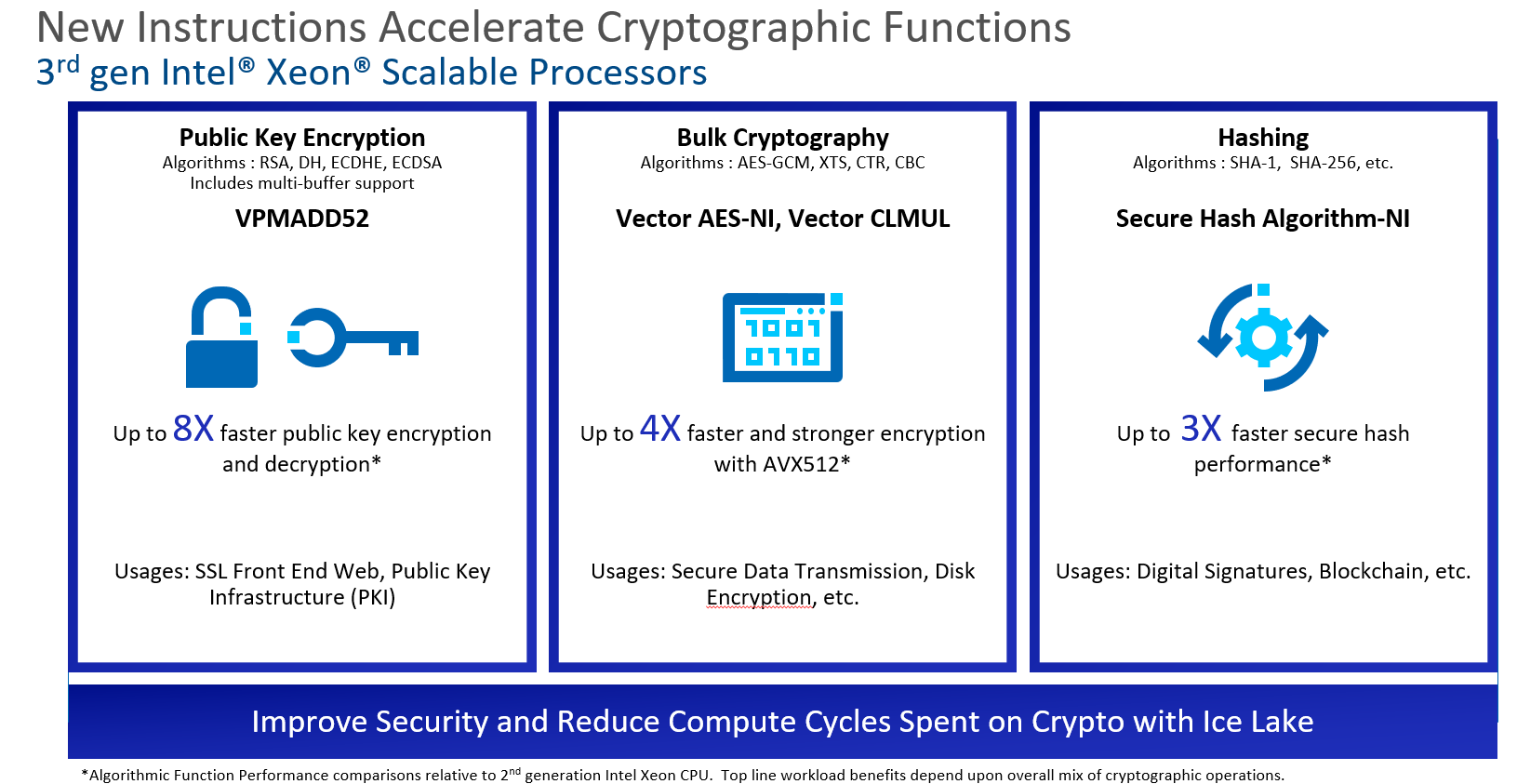
The Bottom Line: 3rd Gen Xeon (Ice Lake) CPUs Improve PoS Blockchains’ Cryptography Performance and Hash Functions
When it is crucial to achieve and maintain the blockchain cryptography performance with ECC-based key system, we found that new Intel Ice Lake x86 CPUs can provide better support for the PoS blockchains which are taking the main stage.
Zenlayer now offers 3rd Gen Xeon (Ice Lake) CPUs through our Bare Metal Cloud (BMC) service. Improve digital experience instantly with on-demand servers and high-performance computing power. To learn more about our blockchain solution, start from here.
References:
(1) http://ethanfast.com/top-crypto.html
(2) High-Throughput Elliptic Curve Cryptography Using AVX2 Vector Instructions, 27th International Conference, Halifax, NS, Canada, 2020