The threat landscape in digital environments is always changing and companies must evolve and adapt. In this guest blog by Jeremiah Fowler, seasoned cyber security researcher with over a decade of experience helping enterprises create responsible security and data protection programs, he shares insights on how collaboration is critical to strengthening defenses against ever-evolving threats.
I have been a cyber security researcher for over a decade and have seen the internal data protection processes and procedures of hundreds of organizations. I know firsthand that there is no one-size-fits-all approach to cyber security and data protection. I have had the privilege of working with many different organizations from Fortune 100 companies to small tech start-ups in the areas of incident response planning, vulnerability identification, and promoting the internal culture of data security.
I believe that Zenlayer’s move to engage with independent security researchers and the wider cyber security community empowers the company to harness external expertise and insights in identifying and addressing potential vulnerabilities. This collaborative mindset not only helps Zenlayer quickly and effectively address security concerns but also fosters a culture of trust and transparency.
One of the great things about collaborating with independent security researchers is that each individual person brings their own specialized experience, skills, and tools. Think of it as adding an additional layer of crowdsourced cyber security on top of Zenlayer’s existing security infrastructure. The more eyes you have looking for potential vulnerabilities in your network or services, the better the chances are of mitigating those risks before they happen or become an incident. I know from experience that a collaboration with independent security researchers allows companies to identify and fix security flaws that may have gone unnoticed during internal testing.
In my opinion, technology depends on humans as much as we depend on it. My area of focus is the human factor of cyber security and how important it is to include people and technology in a multi-layered approach. This is why Zenlayer’s new initiative to collaborate with members of the cyber security community is exciting to me. I was pleasantly surprised when speaking with the Zenlayer team and hearing some of the ways they support the people behind Zenlayer’s products and services. When everyone on the team from the newest developer to senior leadership understands they are not just their job titles, that they are also a data protector, it can make a profound change to the security posture of the organization.
At Zenlayer, human-assisted security is prioritized at every level of operations, from network infrastructure to customer data protection. Software and algorithms are great at automation and identifying a wide range of potential vulnerabilities, but they will never fully replace human creativity and logic. As humans, we think outside the box and create illogical methods to break or bypass protections in ways that AI or software alone can’t (yet). People are an important link that should never be overlooked. This is why Zenlayer’s move to bridge the gap between their internal development team and the cyber security community is a very smart move that is a win-win for both customers, Zenlayer, and the millions of people around the world who rely on their services.
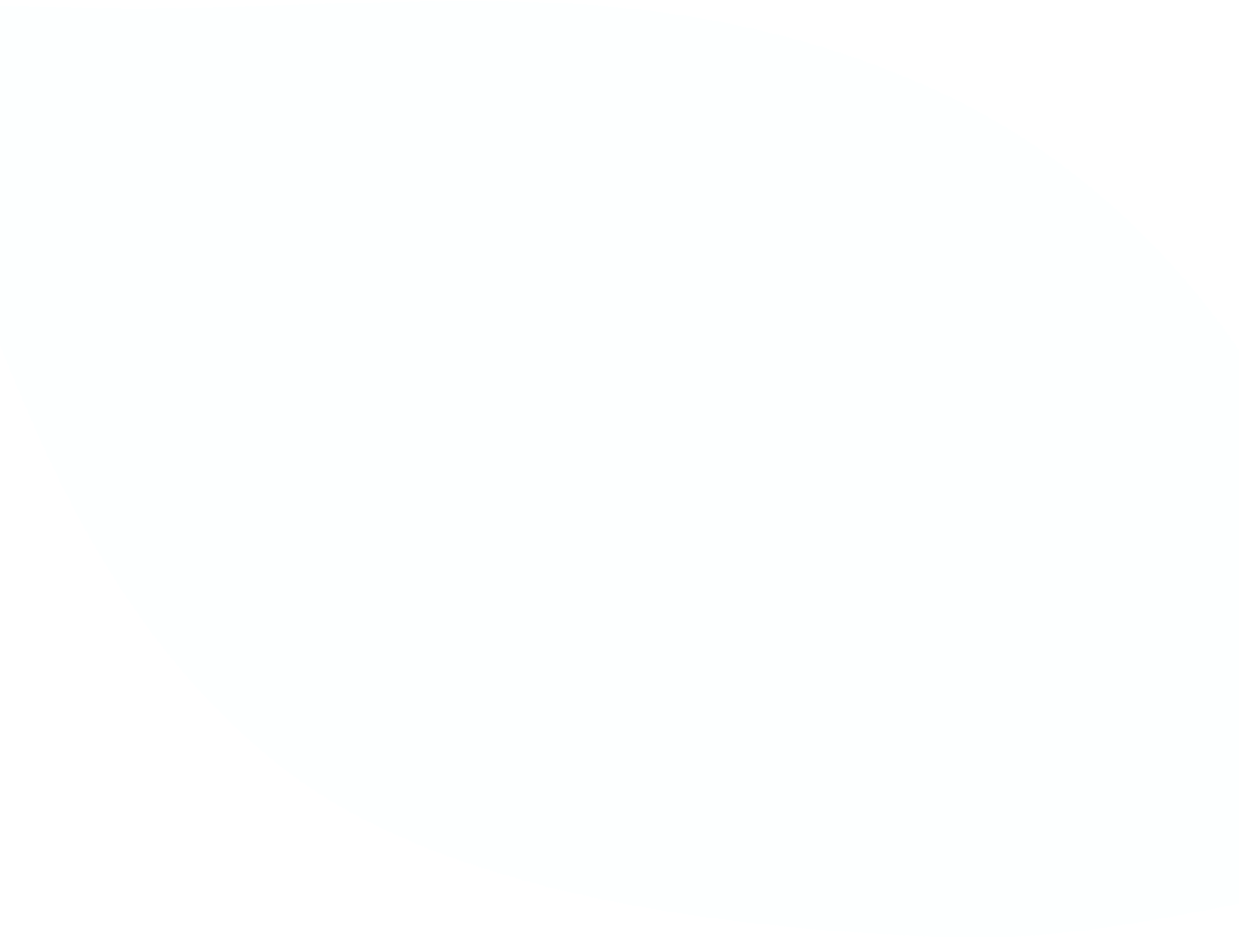
As part of the collaboration with the security research community, Zenlayer has also created a dedicated communication channel where anyone can submit a responsible disclosure notice. This establishes a clear and trusted pathway for security researchers, ethical hackers, and even customers to report any potential vulnerabilities or bugs in Zenlayer’s systems, services, or products. I have personally discovered highly critical vulnerabilities of numerous companies in the past and had difficulty reporting them because there was no way to get a responsible disclosure notice to the right person and the organization offered only customer support contacts. The creation of this dedicated communication channel demonstrates Zenlayer’s commitment to cybersecurity best practices while fostering a culture of transparency, collaboration, and responsible disclosure.
Providing a secure network infrastructure is the core of Zenlayer’s business. It is refreshing for me as a cybersecurity researcher to see any global organization that welcomes outside input when it comes to vulnerability management and community-based penetration testing. I was honored when the Zenlayer team reached out to me to give my perspective, insights, and ask questions. I am also impressed with the collaboration initiative and the addition of a dedicated communication channel for all things security. This shows me that when it comes to issues of data protection and cyber security, Zenlayer is always ready to take a proactive and open door approach.
Zenlayer is currently engaging with Discloze, a vulnerability management and community-based testing firm. The company is also considering establishing a bug bounty program. During this time, submissions can be accepted and will be reviewed on a case-by-case basis. Any ethical researchers and bug bounty hunters are encouraged to report their findings to: disclose@zenlayer.com.